
IAME is a system specifically designed to serve a fragmented identification process based on the IAM cryptographic token. The functionality of the IAME Identity Network will primarily serve as a P2P blocking transaction, but the application can be extended to trade transactions and financial institutions when providing related services.
Problem
Currently, the identification system is not very secure and can provide personal information to third parties. With the current system, people must share their personal information and support documents with the opposing party to identify themselves and their sources of income. Accounts store data at home, more and more people will share with them personal data, so it will be easier to identify and sources of people dohoda.Esli has to do transactions with n-NYM count of counterparty, it is shown in network topology star with n nodes, each of which is a vulnerable place for people sharing data. Technological innovation in encryption mainly works to secure data transfer between two or more nodes in the network, but do not solve the problem of increasing the number of nodes in the network of secret data transmission. Because the number of electronic transactions conducted by a person increases the frequency, the number of nodes in his personal data network increases exponentially, thus increasing the number of vulnerabilities.
Iame Identity Network IAME
identity network is based on 5 main components:
In client;
On the distribution server;
On server checking;
Record in blockade;
On the identity server
Each of these components performs its role in the IAME system, which can be checked by the validation and identification process.
Validation
Process The validation process is a very important operation within the IAME system, with the help of information provided by the client being processed and confirmed by a third party validator.
How this process occurs:
Currently, the identification system is not very secure and can provide personal information to third parties. With the current system, people must share their personal information and support documents with the opposing party to identify themselves and their sources of income. Accounts store data at home, more and more people will share with them personal data, so it will be easier to identify and sources of people dohoda.Esli has to do transactions with n-NYM count of counterparty, it is shown in network topology star with n nodes, each of which is a vulnerable place for people sharing data. Technological innovation in encryption mainly works to secure data transfer between two or more nodes in the network, but do not solve the problem of increasing the number of nodes in the network of secret data transmission. Because the number of electronic transactions conducted by a person increases the frequency, the number of nodes in his personal data network increases exponentially, thus increasing the number of vulnerabilities.
Iame Identity Network IAME
identity network is based on 5 main components:
In client;
On the distribution server;
On server checking;
Record in blockade;
On the identity server
Each of these components performs its role in the IAME system, which can be checked by the validation and identification process.
Validation
Process The validation process is a very important operation within the IAME system, with the help of information provided by the client being processed and confirmed by a third party validator.
How this process occurs:
All client information is fragmented and encrypted into validation packets sent to the distribution server. All of these operations occur at the request of the client.
The distribution server controls the distribution of all packets to a third-party validator, which will return the scan results to the verification server.
After all these procedures, the server checks and evaluates the checks, lists numerical or logical rewards, and interfaces with specific data in the specified lockbox cell.
The distribution server controls the distribution of all packets to a third-party validator, which will return the scan results to the verification server.
After all these procedures, the server checks and evaluates the checks, lists numerical or logical rewards, and interfaces with specific data in the specified lockbox cell.
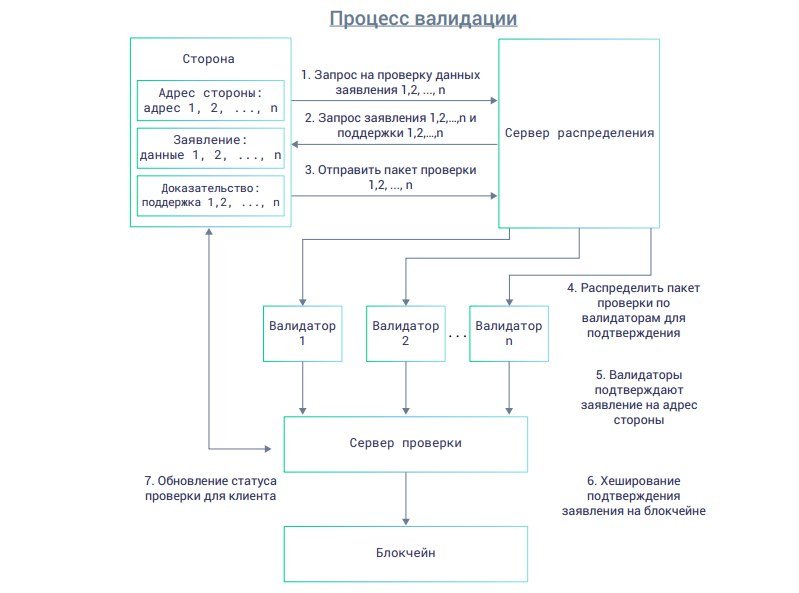
Identification process
To perform operations with partners, the identification process must be completed. This process is based on the requirements of the partners themselves.
To verify a particular transaction, the partner sends a request to the authentication server for the data validation status.
The identification server analyzes the blocks and returns the checked data to the counterparts, after which the partner can complete the transaction.
The IAME identity network will not be used for data exchange between counterparty transactions, it will serve to divide the distribution and verify private information that is not important
To perform operations with partners, the identification process must be completed. This process is based on the requirements of the partners themselves.
To verify a particular transaction, the partner sends a request to the authentication server for the data validation status.
The identification server analyzes the blocks and returns the checked data to the counterparts, after which the partner can complete the transaction.
The IAME identity network will not be used for data exchange between counterparty transactions, it will serve to divide the distribution and verify private information that is not important
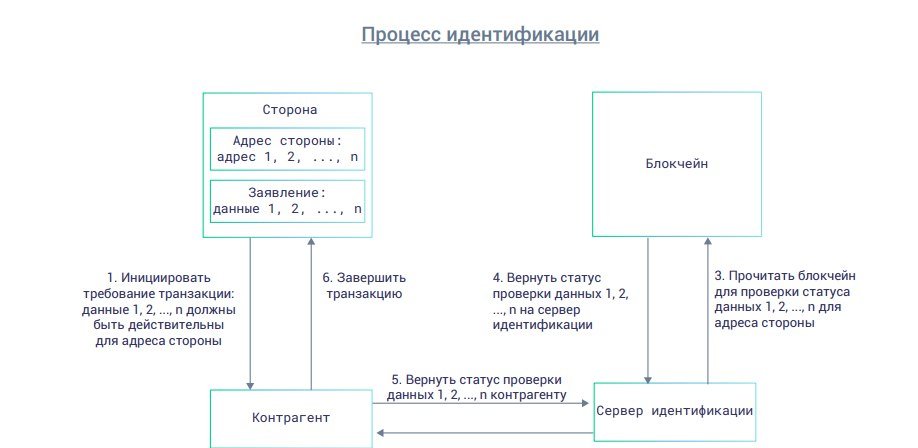
IAM Token
To manage the IAME network, the functional token - the IAM token will be issued, which will act as a verification token to initiate a confirmation request for the validation package on the IAME Identity Network. The parties will spend a token through a client from the IAME identity network, and after deducting the equivalent of a block account's revocation fee, the IAM token balance will be paid as a reward to a third party validator committing a commercial validation process. Thus, tokens will not be an accumulation tool, but will gain market value on the basis of natural demand and supply for the identification process.
The cost of the IAM token will, in fact, be determined by two factors:
The cost of the IAM token will, in fact, be determined by two factors:
The cost of validation, which will be proportional to the financial cost of hashing the amount of data requested in the assigned unit and setting the minimum price for the token.
Market demand, which will be proportional to the demand for identification on the blockade based on the IAME Identity Network. Given the dynamism of data verification in the identification field, market demand will remain cyclical and will only increase with the use of the IAME identity network.
Team
Market demand, which will be proportional to the demand for identification on the blockade based on the IAME Identity Network. Given the dynamism of data verification in the identification field, market demand will remain cyclical and will only increase with the use of the IAME identity network.
Team

Official website
Whitepaper
Roadmap
Price - 1 IAM = 0.0001 ETH
Soft Cap - 1,000,000 USD
Whitepaper
Roadmap
Price - 1 IAM = 0.0001 ETH
Soft Cap - 1,000,000 USD
FACEBOOK | TWITTER | VIDEO | MEDIUM | WEBSITE | TELEGRAM | WHITEPAPER | DRIBBBLE | GITHUB
Authors: YarisRiyadi1st
My Profile Bitcointalk : https://bitcointalk.org/index.php?action=profile;u=1756824;sa=summary
My ETH: 0x8B1820FB5829696cA5b595d09dF4e0F5757a97A7



0 komentar:
Posting Komentar